If you don't know what 2-Step Verification is here is a simple explanation: The two-step system uses both a password and a numerical code tied to your mobile phone, which can be sent by Google via SMS or generated by a smartphone app. Either way, it means a prospective hacker would need to obtain both your password and your phone to access your account.
I’ve been aware of Google’s two-step verification system for some time, but I felt my very strong password, the fact that I don’t use that password anywhere else and that it could not be ascertained by usual social engineering methods, was more than adequate protection. I was also concerned the system might be a hassle to use since I routinely sign in from so many different computers and locations. I already do use a password manager (KeePass) that requires not only a master password but I also use a key file too. [There are other very effective password managers out there I suggest you use one. Ars has a good article about that here.]
But with the massive increase in hacking and high jacking of information and the advancement of brute force cracking technologies and techniques I felt it was time to get onto the 2-step wagon.
Also I suggest that if you use Yahoo mail for anything you migrate towards Gmail or some other ISP. Yahoo has one of the worst records for email security. They are hacked all the time! One recent article is here.
And for petesake please do NOT 'link' your Facebook account with Yahoo - that too is a major source of hacked Facebook account activity. If you currently have it linked I suggest you separate it. You can read how here and here.
So here is a brief explanation of how to enable 2-step verification. I will also link to some other resources on how to enable and use it at the bottom. If you find this too complicated or too much of a hassle you can always disable it very easily.
So let’s get started. Login to your account and go to Account then. Security
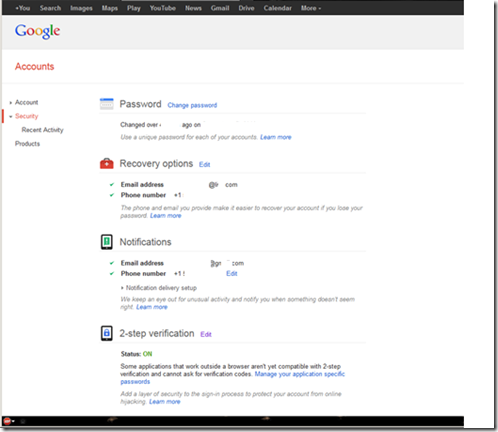
In the Security list you’ll see 2-step verification. This is where you can ‘turn it on’ and edit the settings.
Printable backup codes. Warning: If your phone is unavailable, these codes will be the only way to sign in to your account. Keep them someplace accessible, like your wallet, desk drawer or other safe place. Printable backup codes.

Here click on ‘Show backup Codes’

I printed out a set and put them someplace safe. I also saved them to a text file and imported and copied that text file of codes into my Password management application – KeePass.
If you click on the Application Specific Passwords you can create them for you other applications like Outlook, iMail, ThunderBird etc. Just give it some useful name, click on ‘Generate Password’ and then make sure to copy (or right down) that password – it is only shown once! I just copied each one to a text file so I could then paste them into the proper field (password) on my Outlook/configuration setups.

Some other links and info.
Here's Google's info page. And more here.
Setting up Mac Mail.
Setting up Outlook.
One more thing to consider if you’re a paranoid guy like me. I have all my browsers set to delete Internet history, cache and cookies when I close my Browsers AND I also run CCleaner many times a day to clean out temp files. Doing this will clear out the 2-Step ‘security token’ so you must manually enter some specific cookies to NOT be deleted in your browser and/or CCleaner.
To create ‘safe cookies’ in Firefox here is a good article. For Chrome go here and read the ‘Make exceptions for cookies for specific websites. The method is just about the same for InternetExplorer and Safari.
For CCleaner you can add the cookies to keep manually. Read here.
The actual cookie names you need to keep are here:
accounts.google.com
accounts.youtube.com
google.com
mail.google.com
apis.google.com
0.docs.google.com
docs.google.com
Hope this helps some. Peace out.











